A fresh perspective on how businesses can better prepare for the future through incident response. Written by: Gary Hibberd.
Abstract
Nothing stands still for long and as technology improves and people’s needs outreach technical capabilities, BCM practitioners the world over must be continually looking to see what is on the horizon to understand what we must prepare for.
But what happens when we keep looking at the horizon but ignore what is right in front of us here and now? Cyber risks and social media have been with us for a long time yet there are some who still ignore these areas or simply do not understand how to tackle them.

It is a sad fact that cyber-crime and cyber related incidents are on the increase, so does this change the way that business continuity should approach recovery from such an event? How does ‘cyber’ differ from other kinds of incidents?
Introduction
The world is changing and at pace that few could have predicted twenty-five years ago. But as the world evolves are we as business continuity professionals keeping up with the pace of change?
Many involved in business continuity came into this industry via alternative routes, typically IT or risk/snsurance related disciplines and therefore reasonable to assume have been involved in business for some time. This can lead to institutionalised blindness where corporations, business strategy and dogmatic adherence to ‘due process’ stifle innovation and reduce the potential for identifying genuine business opportunities. Worse still is the potential lack of understanding or appreciation of how information is accessed, used and needed within organisations or by their customers.
For example, over the last forty years we have seen technology move from vast data centres using huge mainframe computers linked to terminals, to the introduction of desktop PC’s and smaller server rooms housed in office blocks. We saw servers moving to centralised SANs and VM’s held in large data centres and the re-introduction of ‘thin-client’. More recent we have seen the emergence of ‘Cloud technology’(!) and the introduction and huge up-take of mobile or ‘Smart’ devices. Some of this is simply a re-engineering/re-branding of old ideas but the fact remains that this reliance requires fresh thinking.
Of course business continuity is about more than just technology and whilst the BCI has developed an elegant description of what BCM is, in truth it is in essence about taking proactive measures to protect the future of the business or organisation. The financial stability or reputation of the business/organisation is ‘why’ we are concerned with BCM.
As business continuity professionals we must seek to understand what risks are on the horizon and understand what they mean to our business.
I believe BCM Professionals today require some fresh thinking to ensure we help our businesses better prepare for the future and one of the key areas requiring fresh ideas is in response to ‘cyber risks’ and cyber related incidents.
Cyber Risk

Although the idea of connecting computers together was born back in 1969 when two nodes of the ARPNET were first connected, it wasn’t until 1989 when Sir Tim Berners-Lee wrote a paper discussing a more comprehensive and elaborate system of connecting computers that the idea of a truly connected society was fully realised. In 1990 a new hyper-text project called ‘WorldWideWeb’ (commonly called ‘web’) was unveiled and the Internet was truly born.
In just twenty-five short years the world has moved from small clusters of computers housed in large data-centres or server rooms communicating directly with one-another, to the globally connected society in which we now live. The speed of change has been truly astounding and each of us individually and collectively are playing catch-up on a daily basis. And with the demand for services over the internet showing no signs of slowing down we are simply running faster to stand still.
Businesses regardless of size, maturity or industry face a vast array of risks. Risks come in many forms including commercial or financial risk, market risks, legal risks, operational risks and many more. This is a bewildering array of ‘risks’ so little wonder many organisations are simply at a loss of what to do or how to protect themselves from what appears to be a new risk.
The term ‘cyber’ has come to mean many things but the risk at least in part has been around for many years. We should remember that the term ‘cyber’ actually has no real meaning except to describe ‘technology’, with only Cybernetics (control of speech and functional processes) having any real basis on fact. Cyber-space, cyber-dating, cyber-cafe, cyber-bullying, cyber-sex, cyber-security and cyber-crime all refer to the act of carrying out some form of activity via a computer. Therefore ‘cyber risks’ are simply risks associated directly with computers.
The BCM Problem
For many years, BCM Professionals have developed IT Disaster Recovery (DR) plans to reduce the impact or likelihood of loss of computer systems in Data Centres. We helped develop elegant backup solutions or resilient networks, using load-balancing or fail-over services to ensure continuity of operations. We agreed to recover systems within tight SLA’s and we helped to establish sensible Recovery Time Objectives (RTO), Recovery Point Objectives (RPO) and Maximum Tolerable Periods of Disruption (MTPD)
In recent years our thinking about ‘cyber risk’ has become focused on the concern around ‘Hackers’ and cyber-terrorism, which is of course an area of this risk and one that should not be ignored (and we will return to). In truth we have lived with cyber-risk for a long time but it has like many things become more complex and come to mean different things to different people.
Virtually every business today is facing the threat from cyber risks no matter what market sector they operate in. Small, medium or large, if they use a computer, if they rely upon information in any way, shape or form cyber-risks are real. Whilst this has always been true what has changed are the customer’s expectations.
Historically the threat to IT systems has come from the ‘physical’ and tangible threats such as fire, flood, loss of power or deliberate sabotage. BC Plans have reflected the need to recover systems quickly and focused upon processes which would recover systems within agreed time-frames. These risks traditionally centred on technical infrastructure we understood; managed or controlled within strict guidelines. Our risk approach was to implement physical controls to these physical threats; generators, Uninterruptable Power Supplies (UPS), fire suppression, water or moisture detection systems and CCTV were also used to reduce the impact or likelihood of an event occurring. Business continuity plans focused on getting the business to Continue as best it could.
Increasingly customers are not willing to wait in a queue no matter if that queue is on a telephone line or on the internet. If a website doesn’t load in five-seconds then there is a strong likelihood that they’ll go elsewhere. If the phone isn’t answered after a few seconds or we are placed ‘on hold’ we are likely to hang-up. Although it can be said this has always been the case, the way in which customers access your services has changed dramatically over recent years. ‘Smart’ devices (aka ‘mobile devices’) have meant that accessing bank accounts, emails and online stores is now something a customer may want to do at any time of the day or night. 24x7x365 Availability is now the expected ‘norm’ and in the eyes of our customers, ‘Continuity’ means less and less.

Added to this problem is the matter that customers not only expect 100% availability of ‘their’ information, but they expect YOU to hold it securely. We therefore must work closer with others such as our Risk & Compliance functions and most certainly Information Security departments.
Information Security is vitally important and needs to include Incident response (aka Crisis Management) to ensure we ‘join the dots’ so that management of incidents doesn’t fall through the gaps. The cyber-risk is one which Information Security practitioners may believe they own and is there’s to manage. However in truth, the role of the Information Security practitioner is to ensure measures are in place to ‘Prepare and Prevent’ incidents occurring, whilst the role of the business continuity practitioner is to ‘Respond and Recover’ for incidents that could and have occurred.
Some reading this may feel that they are too small to either have an Information Security, Risk & Compliance and business continuity function or may feel that cyber-risk does not concern them, but this is where they are most certainly wrong.
Firstly, the task of considering and preparing for cyber-risks (and all risks) rests with the Board and dependent upon the size of the business, the management and implementation of appropriate controls can rest with one or two individuals. There is no need to create a whole industry or department to manage this. Information Security, risk and business continuity management CAN be outsourced (if thought through appropriately).
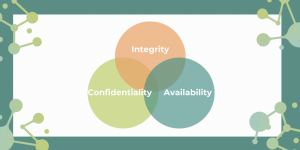
Figure 1: Info Security: CIA – But this applies to BCM and good Risk Management too.
At a time when many (small) businesses don’t seem to think they are vulnerable to cyber risks, UK Intelligence Services released a report in early 2013 stating that the UK is subject to as many as 1,000 ‘attacks’ every hour. These can be simple ‘phishing’ scams or direct hacking attempts to break into a PC or network with the ultimate aim of gaining access to personal and private details. In 2012 cyber-crime was estimated to have cost the country £35 billion (these are both direct and indirect hard and soft costs) with the average cost to each victim of approximately £247 per event. But the key issue is one of perception. Many small, medium and even large organisations simply believe they aren’t a target for ‘cyber-crime’.
Yet, there are many who believe that cyber-risks are a concern only for the multi-national businesses or organisations; Banks, building societies, National institutions like the Government, MI5 or NASA. These are the targets many believe are on the radar of the cyber-criminal, but to think this is naive and leaves us vulnerable. From the smallest accountancy or law firm to the largest travel company or IT service provider, each of us relies upon computers and information to run our business.
Is a small business employing 100 people, using online ordering, banking and financing more or less at risk from cyber-criminals than the large bank it uses next door? The bank will most likely have sophisticated security controls in place with many processes in place to protect itself from physical or technical attack. Will the small business have the same processes in place?
If you were going to try and break into a business to steal from it, would you choose the bank or the business? Where do you think your greatest chances of success rests? What if you were just starting out and needed to practice a new hacking-tool? You may be starting out as a ‘hacker’ and wish to practice.
Would you test out your skills on the bank or the business?
Cyber-criminals rarely wake up one morning and decide to break into a Government system or business like SONY. They build up their skills practising on law firms, accountants, small shops, bakeries, suppliers, builders, photographers, computer firms and anyone else they can try out on. Will they always be successful? No. Will they get caught? It’s doubtful.
SMEs are the cyber-criminals’ playground.
What should we be doing?
Is this indeed a new problem we face? No. But because our client’s expectations and our business needs have changed over recent years our response to the potential threat needs to be re-assessed.
Threats we face from cyber-space have increased and continue to increase as technology becomes more diverse and the need to share more information, faster with greater flexibility. Our response needs some re-thinking and we will be better placed to address the issues we face.
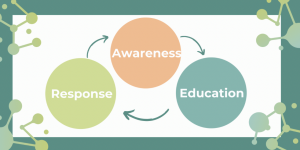
- Aware: Understand your threat landscape
As always, understanding what your vulnerabilities are is the first step. The response “We’ve outsourced our IT to the Cloud.” (or any variation of this) is not acceptable. The Cloud exists – Where is it? What kind of Cloud is it (private or public)? How is the information protected? Who is the Outsource provider? It is important to be aware of new technology your business is using to serve its customers but more than this we must seek to understand HOW our customers are accessing and using their information. Work closer with your business to understand the wants and needs of the customer and then establish how to best respond to these needs.
Understand who might wish to target you and accept the fact that simply owning a computer puts you at risk. Connect it to the internet and you are opening yourself (and your business) to risk (current figures are that within 20 seconds of an unprotected PC being connected to the internet it has been targeted and indeed infected by a virus) . Be aware that one of the more prominent hacker groups ‘Anonymous’ has its very own slogan; “expect us.” The warnings are there so don’t ignore them.
- Educate: We all have a responsibility.
Ensure everyone understands the importance of cyber-security and any potential cyber-risks your business face. This education starts at the top of the organisation and filters all the way down to each and every employee. Remember a large percentage of data breaches (or reputational incidents) are achieved not through amazing feats of computer ‘hacking’, but by exploiting weak passwords, poorly patched computer systems or using mobile devices which have been lost or stolen. Imagine how potentially damaging it would be if you lost your mobile phone (which had no password) only to discover that I had emailed all your contacts and told them I had access to all their data?
- Respond: You may have a CMT but do you need CERT?
Include an element of cyber-risk to your senior management CMT exercises so they understand what the risks are and how best to respond. Do you also have or need a ‘CERT’ (Computer Emergency Response Team) who would respond if there was a security breach? Would anyone know how to shut the floodgates? Cyber security breaches could literally mean millions of pounds in data lost or damaged. Remember that you may not be the intended target. Could someone use your systems to attack one of your clients or customers?
A CERT can be in place to make the big decisions and pull the trigger with a minimum of information and next to no time to operate. They will need to be exercised too so that they can practice how to respond to this risk.
Conclusion
I started this paper by stating that the world of Business Continuity Management is changing and of course this is true. As technology improves and diversifies the need for continuity increases, but it increases in line with the need for greater security. It increases in line with the risks posed not only by those wishing to do us harm (the cyber-criminals) but by those wishing to use the services we offer.
Business continuity has moved towards or accelerating towards service availability at a rate few could have imagined ten or twenty years ago.
Websites which ‘crash’ due to “extremely high levels of traffic” are viewed negatively by those simply wishing to purchase tickets for the latest concert or buy the latest ‘must have’ product. Does the user care if the reason the site is down is due to a DDOS (Distributed Denial of Service) attack or due to many people trying to buy tickets? No. Should systems and processes be better prepared for such an event? Yes.
It was once said that having business continuity was a business differentiated, but as we progress to an ever more diverse yet connected world this need is no longer seen as a ‘nice-to-have’, but a business imperative.
I believe that the changing world of Business Continuity Management can still use all the tools we have right now at our disposal, but we must embrace new technologies (such as social media sites), recognise the needs of the business and the risks they present (cyber-risks) and look outside our own discipline and embrace the good work carried out by others, looking to achieve what we ourselves are looking to achieve (through the adoption of ISO standards).
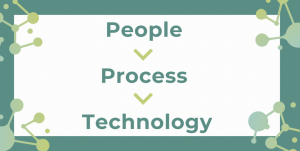
The Business Continuity Management world is changing and all we need to do is accept this and change with it but as we do we need to remember to focus on people, followed by process and finally technology. That’s the only way you’ll build a robust incident management Process. Good luck.
