Introduction to Network Forensics?
Network forensics is a sub-branch of digital forensics relating to the monitoring and analysis of computer network traffic for the purposes of information gathering, legal evidence, or intrusion detection.
Learning Outcome
- You will be able to upload and analyse pcap file using wireshark.
- You will be able to explain filtering techniques and interface selection.
- You will be able to develop skills to identify patterns in network frames that indicate malicious activity.
- You will be able to analyse network frame behavior to detect unusual or suspicious communication patterns.
- You will be able to explore how to analyze payload data within network packets to identify sensitive information.
Tools
Kali Linux VMware/VirtualBox: https://www.kali.org/get-kali/#kali-virtual-machines
Wireshark – Pre installed within kali linux.
Analysing Network traffic for user creation activity.
- Activity 1: Obtaining details of the .pcap file
- Copy the folder “NetworkForensics” into the virtual machine desktop.
- Open wireshark.
- Next, click on File menu and select Open to load the “rogue.pcap”.
- Under the Statistics menu, explore the following options to answer the questions below.
- Capture File Properties
- Protocol Hierarchy
- Communications
Questions:
- When was the pcap file captured (Answer should be in the format YY- MM – DD)?
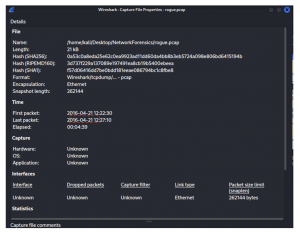
Answer: 2016-04-21
- What is the version of the protocol captured within the pcap file?
Answer: Internet Protocol Version 4 (IPv4)
- Which frame has 28 packets?
Answer: Data
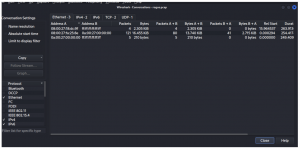
- How many packets did address 0a:00:27:00:00:00 send to 08:00:27:fa:25:8e ?
Answer: 41
Walkthrough:
Looking through the capture properties of the pcap file, we can determine that the file was captured on 2016-04-21.
Looking through Protocol Hierarchy of the pcap file, we can determine the version of the captured protocol which is IPv4 and data frame has 28 packets.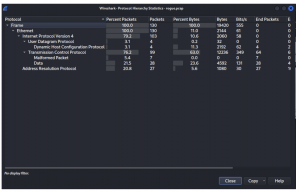
Looking through the Conversation option, we can determine the communication between the endpoints. As shown below, there were 41 packets sent across the communication between address 0a:00:27:00:00:00 to 08:00:27:fa:25:8e.
Activity 2: Analysing frames for malicious activity.
- Filter the pcap file to view frames marked as data. Ensure your display column is also include “stream index” view.
- Right click on the frame and select Follow -> TCP stream to search for communication in relation to user creation via remote shell access.
Questions:
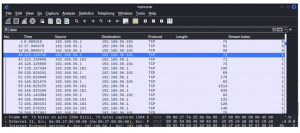
- How many “stream index” value was displayed?
Answer: 2
- What is the stream index value of frame 4?
Answer: 0
- Stream 1 starts at which frame?
Answer: 40
- What was the date the attacker remotely accesses the system?
Answer: 21st April
- What is the username and password of the rogue user account created?
Answer: Username: marcelle
Pasword: password
- What was the command executed by the attacker after creating a rogue account
Answer: cat /etc/shadow
Walkthrough:
Applying the filter “data” and customising the display to include “stream index” helps in analysing communication between two nodes. We can see from the below image that there are two stream index value in this case. Stream 0 start at frame number 4 and stream 1 starts at frame 40.
Looking at the TCP stream of index 1 showed a possible remote shell access activity whereby commands such as whoami, finger, ls, and cat were ran. It also appears that a file titled “passhash.txt” displayed an output of the /etc/shadow file.
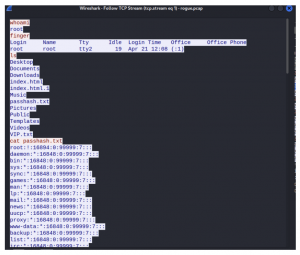
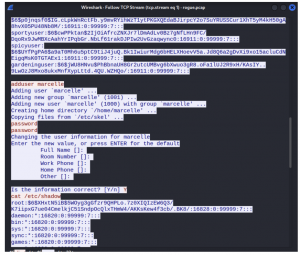
Further analysing the TCP stream of index 1 window showed that an adduser command was used to create a user by the name “marcelle” with a password “password”. The command /etc/shadow file was run to validate if the user profile “marcelle” was successfully created.
Part 2: Simple FTP pcap challenge
- Open the file FTP.pcap in wireshark.
- Analyse the pcap and answer the following questions.
Questions:
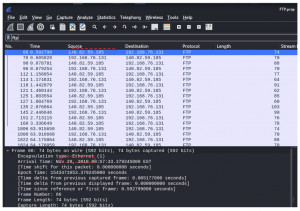
- What is the IP address of the FTP server
Answer: 140.82.59.185
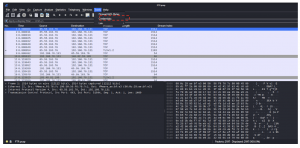
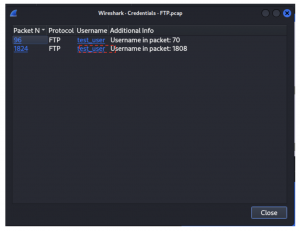
- State the packet numbers that contains the password?
Answer: Packet Number 96 and 1824
- What is the username and password of the FTP Server?
Answer: Username: test_user Password: Nipun@123
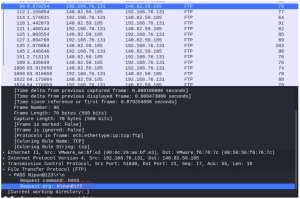
- What date did the user attempt to access the FTP server? (Answer should be in the format YY- MM – DD)
Answer: 2018-11-29
Walkthrough: