
Introduction to Mobile Forensics
Mobile forensics is the process of recovering digital evidence from mobile devices using accepted methods. Unlike traditional digital forensics processes, mobile forensics solely focuses on retrieving information from mobile devices such as smartphones, androids, and tablets.
Learning Outcome
- You will be able to create a new case on ALEAPP and iLEAPP (Forensic tool).
- You will be able to explain the types of data sources ALEAPP and iLEAPP can analyze, such as mobile Logs, Events, and Protobufs.
- You will be able to describe the structure and content of Android ad iOS Logs and Events.
- You will be able to analyze parsed data to identify user activities, application usage, notifications, and system events.
Tools
Kali Linux VMware/VirtualBox: https://www.kali.org/get-kali/#kali-virtual-machines
ALEAPP v3.1.8: https://github.com/abrignoni/ALEAPP
iLEAPP v1/18.7: https://github.com/abrignoni/iLEAPP
Setting up ALEAPP & iLEAAP
ALEAPP and iLEAPP is an open-source tool developed by Alexis Brignoni that is able to quickly triage both Android and iOS data collection. It is a cross-platform tool that can be run on any major operating system that supports Python, we are going to use it on Kali Linux. You may refer to the links provided above for guidance to install ALEAPP and iLEAPP
Part 1: Android Forensics Analysis using ALEAPP
- Copy the folder “Mobile Forensics” into the virtual machine desktop.
- Unzip the “Android Logical Image” folder.
- Create a new folder called “Android”. This folder will be selected as the output folder to store the parsed files.
Open the kali linux terminal and navigate to the directory where ALEAPP was installed as shown below.
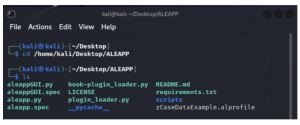
5. Run the below command to execute the GUI interface of ALEAPP.
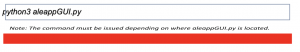
6. You should be able to see the ALEAPP GUI interface.
7. Click the “Browse Folder” tab and select the “Android Logical Image” folder as shown below and click “OK” tab.
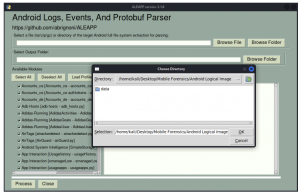
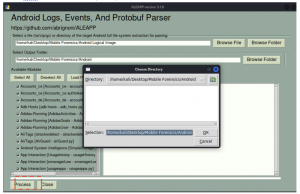
8. Click the “Browse Folder” tab and select the new folder created in step 3 above. Once done, click “OK” tab. Subsequently, click the “Process” below marked in red.
9. Once the process is completed, you will be prompted with the following window. Click the “OK” tab.
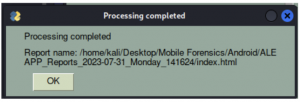
10. Subsequently, the report of the analysis will open on browser automatically.
11. Analyse the information within the report and answer the following questions.
Questions:
-
- State the email address that was logged into the google account of the android device.
- Was there any twitter account information? If yes, please provide the account name.
- Where can we find information related to app launch? (Provide the file path)
- How many apps were launched via the home screen?
- What is the MAC address of the Bluetooth adapter?
- Where there any bluetooth device connected to the android device?
- What software did the user download into the android device?
- When was “fun flag games” was searched? (Answer should be in the format YYYY- MM – DD_HH: MM: SS Timestamp in UTC)
- Does the login data information reveal password details? If yes, list the password disclosed.
- From where was boot.img downloaded?
- Who was Tina Louis chating with via Google Chat?
- What is the SSID of the following Wifi Mac Address 00:00:5e:00:01:03?
- It seems that Tina intended to spawn some office romance as she searched for its legality. What was the article’s title that answered her question? (Hint: dating)
Part 2: iOS Forensics Analysis using iLEAPP
- Copy the folder “Mobile Forensics” into the virtual machine desktop.
- Unzip the “iOS Logical Image” folder.
- Create a new folder called “iphone”. This folder will be selected as the output folder to store the parsed files.
- Open the kali linux terminal and navigate to the directory where iLEAPP was installed as shown below.
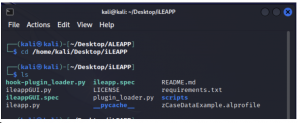
- Run the below command to execute the GUI interface of ALEAPP.

- You should be able to see the iLEAPP GUI interface.
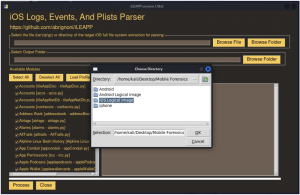
- Click the “Browse Folder” tab and select the “iOS Logical Image” folder as shown below and click “OK” tab.
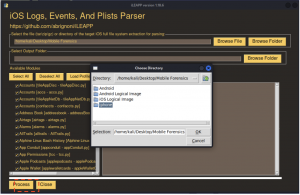
- Click the “Browse Folder” tab and select the new folder created in step 3 above. Once done, click “OK” tab. Subsequently, click the “Process” below marked in red.
- Once the process is completed, you will be prompted with the following window. Click the “OK” tab.
- Subsequently, the report of the analysis will open on browser automatically.
- Analyse the information within the report and answer the following questions.
- Questions:
-
- What is the username of the AppleID of the iOS device?
- What username was used for AllTrails?
- Did Patrick receive any incoming call? If yes, please state the number he received call from.
- Patrick’s iphone was connected to which device?
- What version of iphone was on the system?
- What time zone was used on the system?
- When was the last mobile backup done? (Answer should be in the format YYYY- MM – DD_HH: MM: SS)
- When was “Grocery List” notes created? (Answer should be in the format YYYY- MM – DD_HH: MM: SS)
- What is the name of the GIF sent to Patrick via Bumble message? (Hint: The answer is three words)
- It seems that Patrick’s computer has been hacked. What was the search term he used to get guidance on what action to take?
- Which app was uninstalled from the device?
-
